Fiber optic networks are now the most popular way to communicate over long distances. This is due to their huge bandwidth (more than 10 Gb/s) and low signal attenuation over long distances. However, one of the main advantages until recently was considered the localization of signal within the waveguide core and the practical impossibility of tapping and eavesdropping of the signal by hackers. Is it really an impossible task at the current development of technology? Let’s find out.
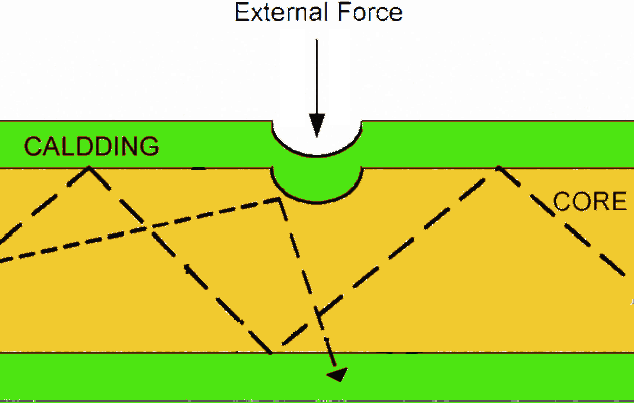
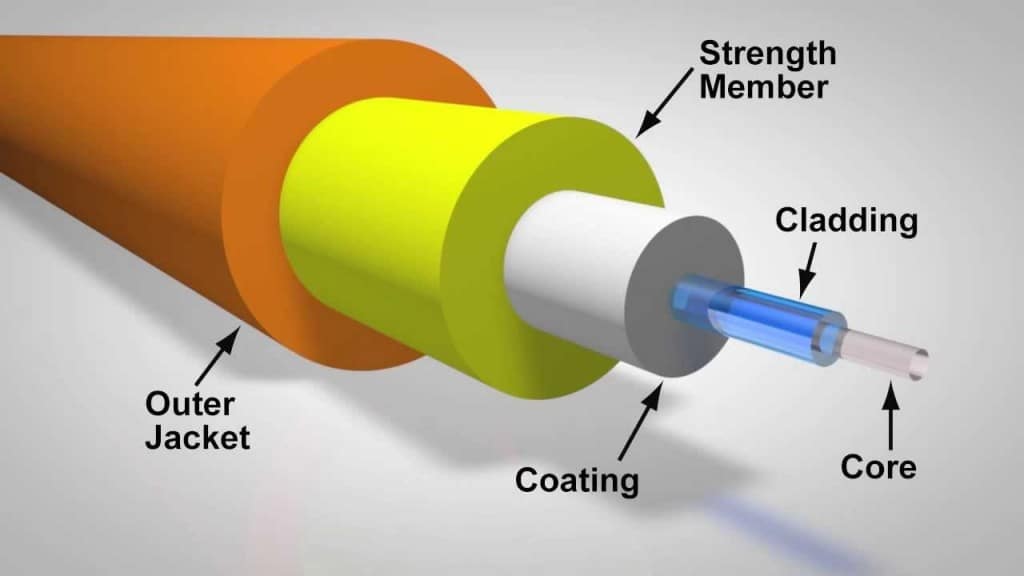
Optical fiber is a thread of glass with a large refraction index (core), surrounded by cladding with a lower index of refraction. The effect of total internal reflection plays the main role in the propagation of light in a waveguide and light is distributed only along the core (as in the picture below).
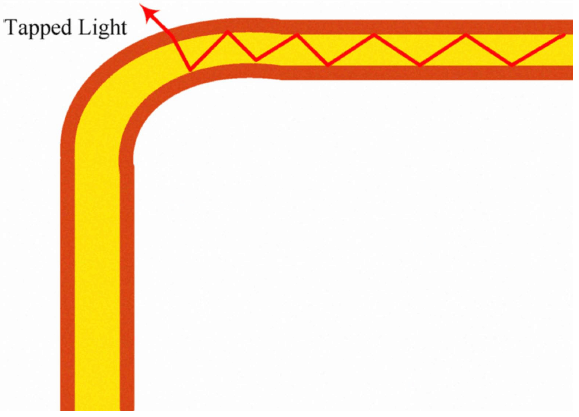
Now imagine for a moment that you’re a secret agent and you’ve got the task to steal a traffic from a fiber-optic network. So, our government is very lucky – you are a very cool agent with a PhD degree in MIT. The first idea that comes to mind, you need to somehow break the conditions of total internal reflection of light within the waveguide. Analysis shows that this is possible by deformation of fiber, so you either create a dot cavity in the volume of the fiber or bend the fiber so that signal would leave the waveguide at the point with a minimal curvature. But there is a small problem: the core’s diameter of a single-mode fiber is usually about 7-10 micrometers, and it is obvious that wrench and screwdriver are not enough to do this. Nevertheless, you have a strong feeling our government would pay a lot for my job, so you proceed.
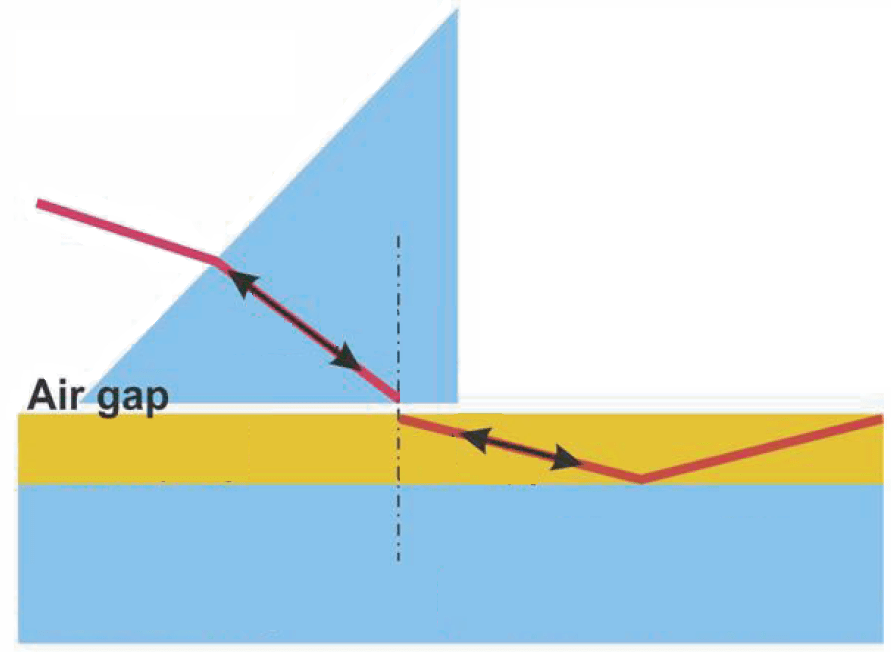
Another method of wiretapping of fiber networks is well known by physicists. The thing is that the electromagnetic field of a wave is mostly concentrated in the waveguide core while the field amplitude in the surface layer decreases exponentially with the distance; this field is known as an evanescent field. The condition of the wave propagation is not performed for the evanescent waves, but if we put the material with large refractive index to the air gap, then there arises an electromagnetic wave (the capture of the desired signal). This effect is analogous to the tunneling of a particles through a potential barrier in the quantum mechanics. Described scheme is the most interesting, since it can work in two directions: receive signals from fiber and inject them into the line. This makes it possible, if necessary, to inject noise in the communication channel – if you cannot eavesdrop, then no one can use it. However, we should mention for the unaware reader about a serious technological difficulties of the method, which represented by high-precision polishing of the surface of the optical fiber.
To protect ourselves from the unauthorized connections, we can include a number of improvements in the communication line such as integration of electrical conductors into the fiber cable whose damaging will trigger an alarm. Or, for example, by measuring the average power in line since the unauthorized connection causes signal’s power attenuation. The most viable is the opportunity of using OTDRs to determine where the loss of fiber possibilities is. These measures certainly increase the cost of construction and maintenance of communications, but if we value the security of networks, there is no other way.
Methods of data encryption can be considered a variant of the budget solution. Although, encryption doesn’t prevent from connecting to the fiber, and only makes a stolen information useless to hackers. Thus, we can conclude that the fiber-optic network, which for a long time was considered a very reliable one, could be compromised by unauthorized connections, and a safety issue dedicated channel again rests on the methods of cryptography.